In our article LLMNR and NetBIOS-NS Spoofing with Responder we stepped you through how to exploit a very common issue on Windows networks. In this one, we’re going to cover how to fix it.
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS-Name Service (NBT-NS) are name resolution protocols that are enabled by default on Windows machines. They’re both used as a fallback for DNS. If a machine requests a hostname, such as when attempting to connect to a file-share, and the DNS server doesn’t have an answer – either because the DNS server is temporarily unavailable or the hostname was incorrectly typed – then an LLMNR request will be sent, followed by an NBT request. LLMNR is a multicast protocol and NBT-NS is a broadcast protocol.
Therefore, an attack can take place where a threat actor responds to these requests with illegitimate requests. For example, directing the requesting user to connect to the attacker’s machine where an authentication attempt will be made – disclosing hashed credentials for the targeted user. Where SMB signing is disabled, which it is by default on Windows machines, these issues can often be combined to lead to command execution against vulnerable machines.
LLMNR and NetBIOS-NS can be used to perform interception attacks, leading to credential theft or even command execution. However, these two articles are not commonly needed on networks and can therefore be safely disabled.
Disable LLMNR
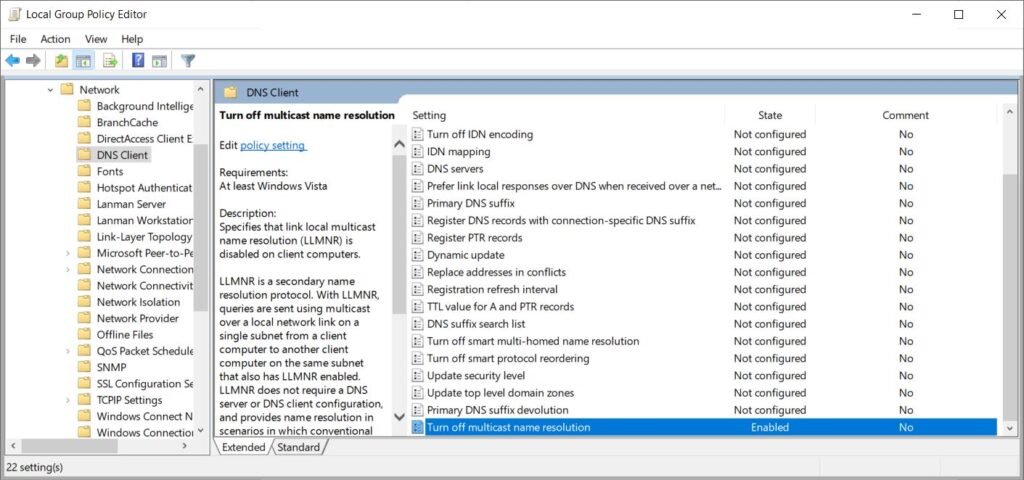
LLMNR can be disabled using Group Policy:
Open Group Policy editor: Start → Run → gpedit.msc
Navigate to DNS Client: Local Computer Policy → Computer Configuration → Administrative Templates → Network → DNS Client
Set “Turn Off Multicast Name Resolution” to Enabled.
Disable NetBIOS-NS
NetBIOS-NS can be disabled either by reconfiguring the network interface manually; or alternatively running a PowerShell command on boot. This can be achieved with Group Policy to automate it across a domain.
Open Group Policy editor: Start → Run → gpedit.msc
Navigate to Scripts (Startup/Shutdown): Local Computer Policy → Computer Configuration → Windows Settings → Scripts (Startup/Shutdown)
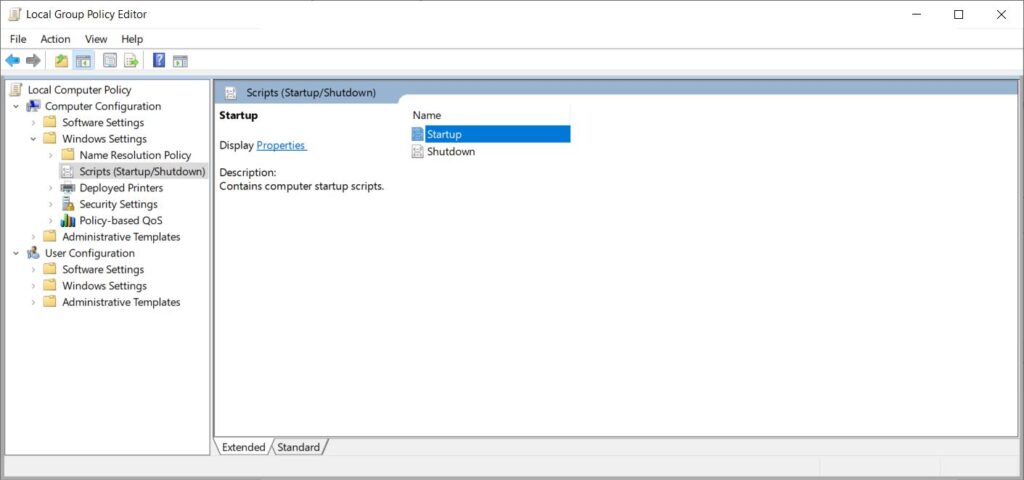
Save the following script into a file:
set-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces\tcpip* -Name NetbiosOptions -Value 2Click “PowerShell Scripts”, click “Add” then select the script you saved.
That’s it!
Read More
Fixing Cross-site Scripting (XSS)
This issue comes about where user supplied input is included within server responses without filtration or encoding. One very effective method of preventing this attack is to use an allow-list (sometimes called a whitelist) which will allow only known good content. For example, if your expected input is an integer [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
